Roadmap of leading practices and “Checklist”
A planning “Roadmap” for cybersecurity risk and prioritisation
04
ENTERPRISE-WIDE CYBERSECURITY
SCOPE OF INTERVENTION FOR EQUIPMENT RENTAL COMPANIES
This guide offers a model and template across the four main areas of a business of our type to scope out, risk assess and prioritise interventions to optimise cybersecurity strategy.
All companies are different, all at different stages, all with different needs and budgets and many following adopted frameworks and strategies, but we hope this model, compiled from combined experiences of leaders in our sector may be a useful “Roadmap” for those at base levels and a “Checklist” for those maturing their security to ensure all areas are covered.
Leaders emphasise that, whilst a comprehensive security plan forms an essential part of an overall business strategy, “an over-arching plan” does not have to be the very first step – a full plan may typically come in maturity stages. It is most important in early stages to take steps to identify all possible high risk areas in the business and prioritise actions to plug or patch vulnerabilities.
A comprehensive scan of risks across each of the four elements outlined in this guide as a checklist can be a good starting point.
As high risk areas are dealt with, medium areas can then be tackled. It is important to say that research indicates that, from a base level, moving up to cover all significant risk areas to leader levels, can be a three to five year process, requiring material and sustained investment.
Each organisation should do what is appropriate to the risk assessment of their security – not necessarily “to reach for the stars”.
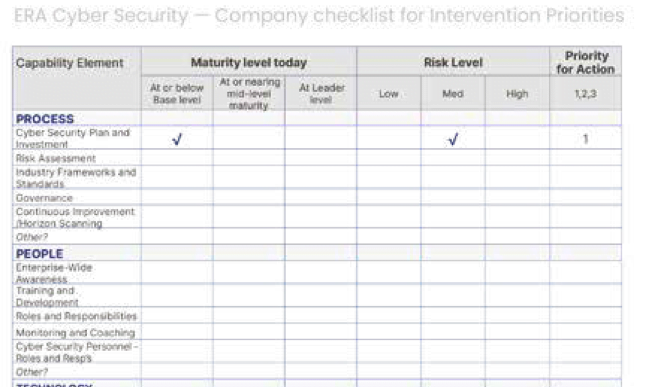
A checklist for scope, risk assessment and prioritisation based on the four elements in the roadmap is included as a useful template seen here.
“You get what you measure…
Leaders report that it is essential to ensure key areas of performance that impact your cybersecurity status are measured with Key Performance Measures (or Indicators) (KPIs) in place. The roadmap in this guide also indicates typical measures and performance measurement systems in use today by leader companies.”
The focus for cybersecurity interventions is often around technology and systems. However, many risks have root cause in human behaviour, robustness of processes and monitoring, reporting and responses within the enterprise.
According to equipment rental leaders in this field, an organisation needs to consider an enterprise-wide strategy to ensure all areas of vulnerability are considered.
Each organisation will have different risks, scope of operations and gaps, however leaders consider that a checklist for a comprehensive scope can be captured under four capability elements covering:
> PROCESS
> PEOPLE
> TECHNOLOGY
> INFRASTRUCTURE

WHILST EACH COMPANY WILL HAVE DIFFERENT APPROACHES AND PRIORITIES, THIS FOUR FACTOR MODEL PROVIDES AN ENTERPRISE-WIDE “CHECKLIST” OF ELEMENTS TO CONSIDER…
CYBERSECURITY WITHIN EQUIPMENT RENTAL COMPANIES
“ENTERPRISE-WIDE” INTERVENTION
CUSTOMERS
PROCESS
- Cybersecurity Plan and Investment
- Risk Assessment
- Industry Frameworks and Standards
- Governance
- Continuous Improvement and Horizon Scanning
TECHNOLOGY
- Inventory Management
- Firewall Management
- Secure Configuration
- User Access Control
- Malware protection
- Security update management
- Distributed Networks
- Threat and Health Monitoring
STAKEHOLDERS
PEOPLE
- Enterprise-wide Awareness
- Training and Development
- Roles and Responsibilities
- Monitoring and Coaching
- Cybersecurity Personnel – Roles and Responsibilities
INFRASTRUCTURE
- Policies and Procedures
- Communications
- Emergency Response
- Customer Management
- Supply Chain Management
- Maintenance
CYBERSECURITY IN EQUIPMENT RENTAL COMPANIES
MATURITY STAGES
Features of each maturity level:
Also see section on “Leading practices examples– Process”
*Refer to: About Cyber Essentials – NCSC.GOV.UK
**Refer to: Cybersecurity Best Practices (cisecurity.org)
Also see section on “Leading practices examples – People”
Also see section on “Leading Practices examples – Technology”
*Refer to: Enterprise Security Solutions | Splunk
**Refer to: Azure Sentinel – Cloud-native SIEM solution | Microsoft Azure
Also see section on “Leading Practices examples – Infrastructure”