Leading practices illustrated
Basic, advanced and leader practices, illustrating the roadmap
06
Cybersecurity
LEADING PRACTICES
Leading practices – Process – Inventory and risk assessment are the first steps.
Leaders stress that it is more important in early stages to take steps to identify all possible high risk areas in the business and prioritise actions to plug or patch vulnerabilities. A comprehensive scan of risks across each of the pillar areas in this guide can be a good starting point.
"Leader view: strategy driven by risk assessment
Comprehensive and multilayer defence systems require significant investments from the company, which might not be appropriate to the risk involved. Customised systems are best suited for a particular company, individual level plans. Large cyber defence systems at group level attract attention – it‘s better to have smaller defence systems at local level with limited security layers at central (group) level. Every new project should have its own security measures, on top of a central or horizontal system.
Having decentralised IT systems can in fact decrease vulnerability, as the attacker cannot gain control over the whole system (and multinationals should not have a single, centralised global defence HQ. Individual companies should not have a one-size-fits-all approach, but custom made plans). In the event of a security breach, decentralised systems mean it can be limited to one branch or unit, giving the hacker limited advantage and benefit, allowing time and limiting impact while the breach becomes visible to the whole company and the breach can be “quarantined” and closed down.
So knowing all your assets first, defining points of highest risk, setting a control and response strategy aligned to the risk profiles and then prioritising actions is the key to successful defence.”
PROCESS
“We don’t seek the uItimate incybersecurity. We do risk assessment based on the assumption that it should be more difficult for a hacker to crack our systems than the systems of other targets, like our competitors.”
Leading Practices – Process – Enterprise-wide accreditation frameworks
Leaders in our industry point to a basic, better, best type of journey to arrive at fit for purpose security, that may use formal accreditations as milestones or be custom built in- house and follow the same principles. A number of international frameworks are in use, two commonly quoted by leaders include:
CYBERSECURITY ESSENTIALS, COMBINED WITH ISO 27001 *

Self-certified UK Government scheme to demonstrate commitment to cybersecurity

Cyber Essentials with hands-on external technical verification from IASME consortium. Often requested in RFPs in some countries
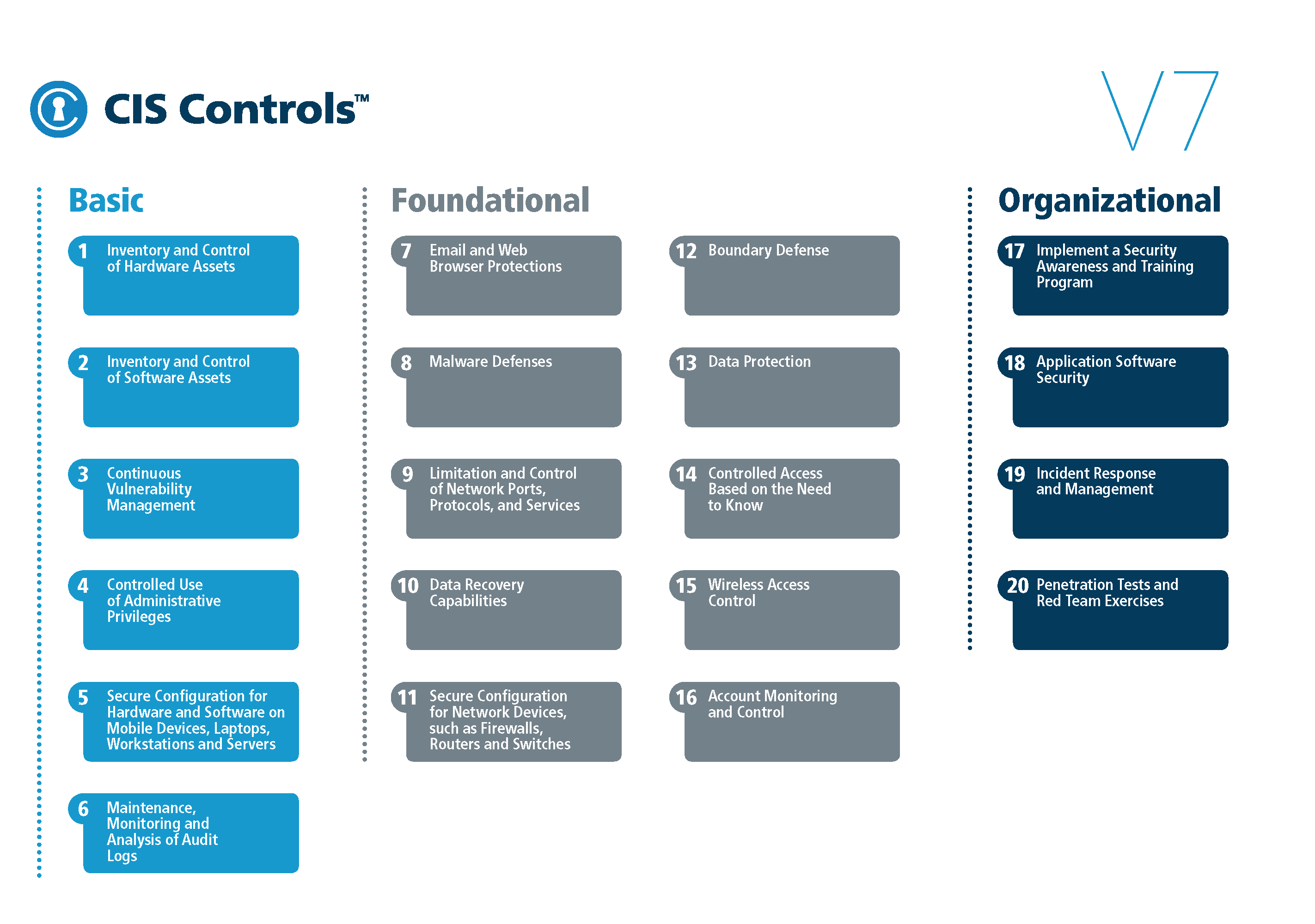
“CIS CONTROLS” **

ISO27001 is an international standard on how to manage information security. Often requested in RFPs in some countries

On 24th January 2022 the NCSC and IASME implemented an updated set of requirements for Cyber Essentials. This update was the biggest overhaul of the scheme’s technical controls since it was launched in 2014 and came in response to the cybersecurity challenges organisations now regularly face.
*Refer to: About Cyber Essentials – NCSC.GOV.UK
**Refer to: Cybersecurity Best Practices (cisecurity.org)
Leading practices – People – Cybersecurity is not an “IT thing”
There is an important role for Human Resources Management (HR) in cybersecurity defence. Scope of HR intervention and support in leader companies includes:
- Design and development of policies and procedures (including GDPR and data protection protocols) and their communication to all
- Adaptation of employee terms and conditions and role descriptions to include data and security responsibilities.
- Enterprise-wide awareness and training on cybersecurity imperatives.
- Training needs analysis for front line roles and specific security personnel. Leaders carry out a mix of in-house training courses and use of external training specialists, particularly where accreditations are being sought.
- Communications media such as newsletters or social media bulletins to broadcast latest trends or threats across the enterprise.
- Set up and hosting of an anonymous “Whistle Blowing” chat or media box to allow staff to signal potential vulnerabilities that they feel may not be being taken seriously.
- Advanced organisations use techniques such as “Phishing simulation” that allows HR to identify retraining or disciplinary needs to address failings in behaviours.
“On the people front, we consider Health and Safety processes as a useful proxy when benchmarking our cybersecurity processes. Electronic safety has many of the same features as physical safety
and creating an embedded culture of “Safety in everything we do” is a key message.
People development and training effectiveness need to be audited and measured in the same way as other elements of cybersecurity.
We use “Simulated phishing” – tools to test whether people are recognising and avoiding traps, by testing response to a simulated trap. If errors are made, individual coaching can be targeted with staff; a sustained high error rate by a staff member over time may require a flag with someone’s line manager to take corrective action.”
PEOPLE
“Computers, networks and software don’t create cyber risks and vulnerabilities. The people who design them, implement them and operate them do. Awareness, roles and responsibilities and training are some of the most powerful and accessible tools everyone has at their disposal to prevent and manage weaknesses.”
Leading practices – People – Cybersecurity is a “People thing”
Train in the essentials and generate awareness first.
Low cost, high impact.
EMBED CYBERSECURITY INTO THE ORGANISATION AND ALL ROLES, ENTERPRISE-WIDE.
MEASURE AND TEST PEOPLE’S COMPLIANCE, UNDERSTANDING AND EFFECTIVENESS.
“Where we have lower skilled or technology averse employees, we adapt to fit human limitations. Paradoxically, using paper can be a valid part of cyber protection. Whilst moving processes online and deploying technology and automation is undoubtedly the way things will be, by exception, if we find that it is too difficult for some staff, particularly those in blue collar basic functions in depot or distributed activities to operate a function or send data via online access, reluctantly – we will leave it on paper. Where that is best for cyber safety, that takes precedence.”
Low skilled or remote location staff may need low technology solutions to support cybersecurity needs.
“A lot of people think you can put in technology layer on layer to protect you, but actually simpler and low cost interventions in how you manage people and behaviours can have more impact, especially in the early stages.”
> TECHNOLOGY
Information Technology tools continue to develop rapidly and provide a powerful means of cyber defence, for “early warning” and threat interception.
LEADING PRACTICES EXAMPLE THREAT AND HEALTH MONITORING – SET UP OF A ”SOC”
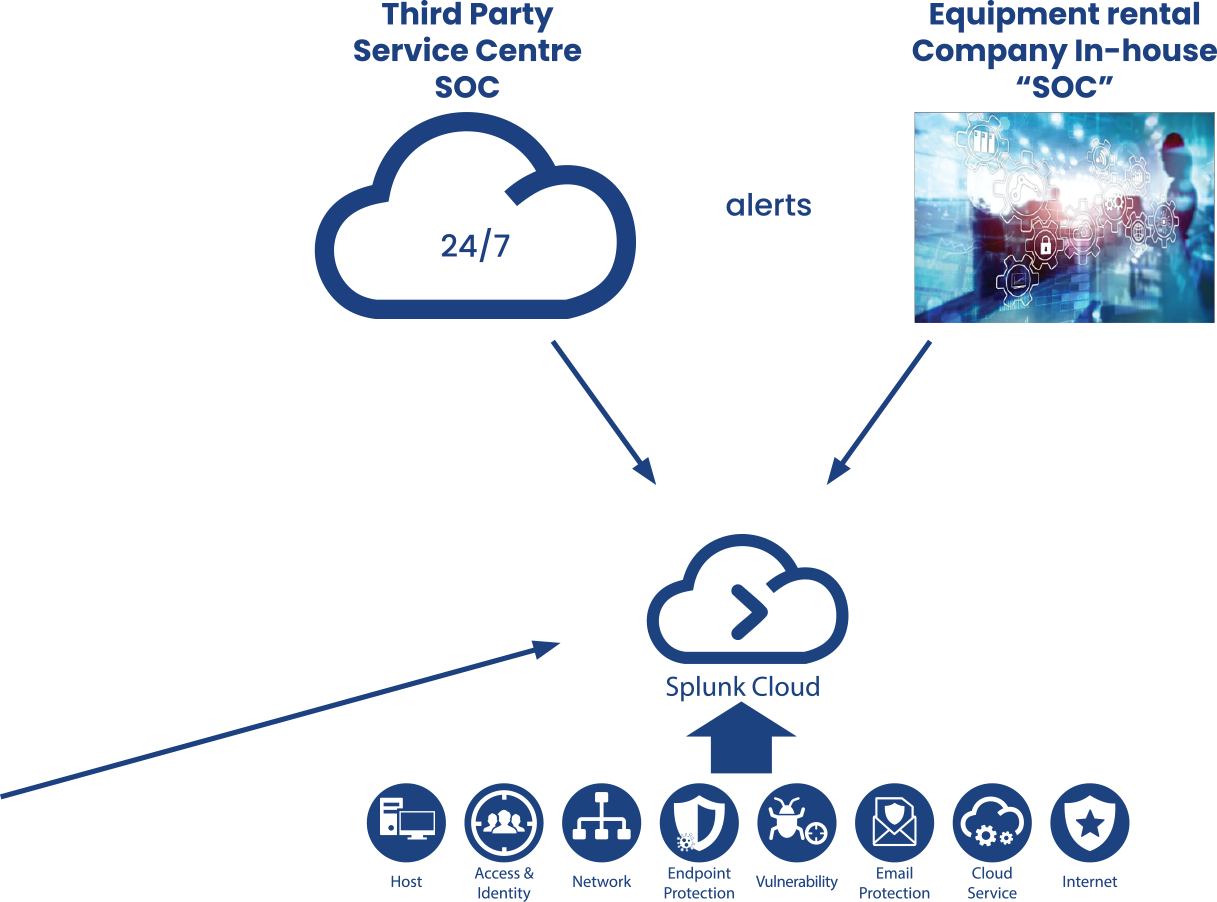
Establishing a “SOC” (Security Operations Centre) is essential to get the most out of the power of automated systems.
Leaders may operate an in-house SOC, often supplemented by third party centres which can offer 24×7 support cover and advanced monitoring and management services.
A shared centre service provided by a third party is also considered a good way for less advanced or smaller organisations to get access to high quality Health and Threat Monitoring, when an in-house one may not be justifiable.
Equipment rental company example: “Splunk”* – Splunk and integrated third party and in-house “SOC” in use, identifying and signalling threats real time across the enterprise
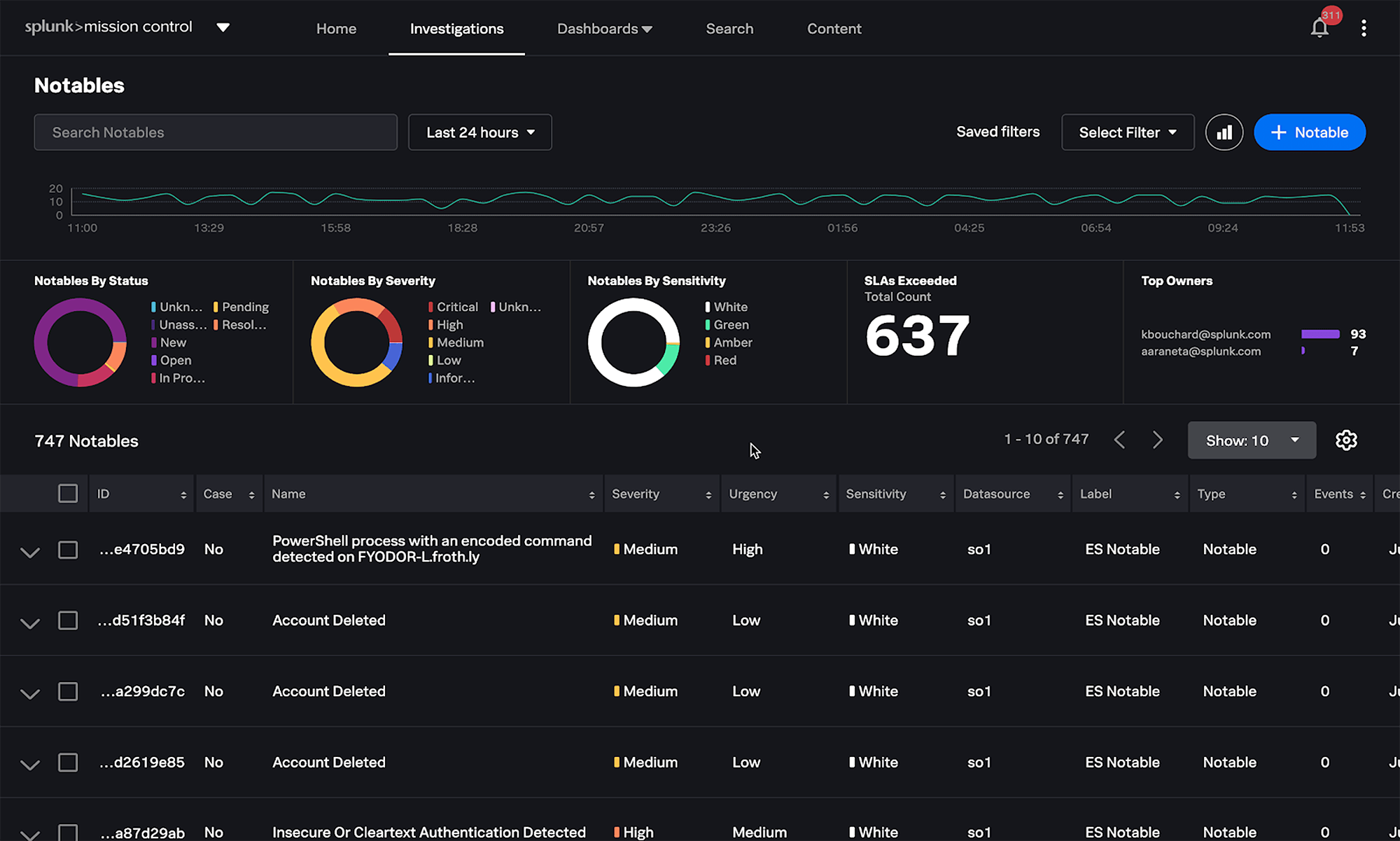
*Refer to: Enterprise Security Solutions | Splunk
- The combined SOC runs on a single Splunk* platform.
- Updated and actively monitored 24×7×365.
- Security Service Provider SOC – support, troubleshooting, development, health monitoring, incident response.
- In-house SOC – ”hourlies” refresh and review, hunts for malicious behaviour, investigates tickets raised by SOC and users.
Threat and health monitoring – Enterprise-wide diagnostics
Most of the leading monitoring and alarm systems are considered effective and valuable tools in the fight against attack. Those most commonly quoted by leaders in equipment rental as in active use are “Microsoft Azure Sentinel”* and “Splunk”*. “MS Azure Sentinel”* identifying and signalling threats across the enterprise.
TECHNOLOGY CAN HELP TO AUDIT THE EFFECTIVENESS OF CYBERSECURITY USER EXAMPLE**
Quarterly audits to simulate attacks and report on company performance can include:
- “OSINT” for Digital Asset Discovery – “Open Source Intelligence” identifies the public attack surface of the company.
- Security Assessment (Blackbox) – Automated audit routines from outside the company, with no inside knowledge.
- Security Assessment (Whitebox) – Audit routines using accounts set up with different permission groups.
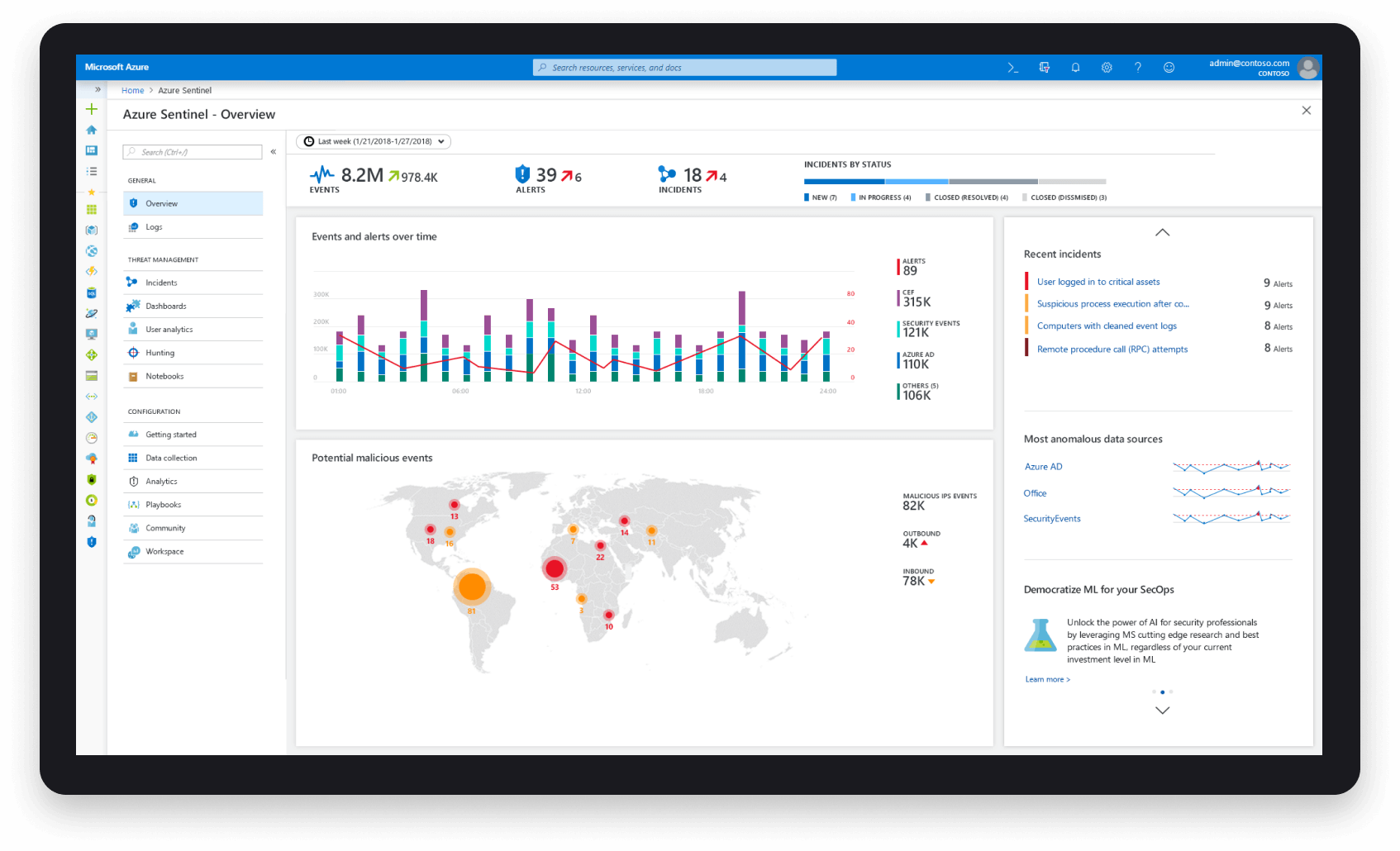
Use of available technology and automation for Health and Threats is crucial… But remember, there is no point investing in the technologies, if you do not also place infrastructure around it to be able to respond on a “24 x 7” basis. Hackers don’t work office hours, so what happens if the system alarms sound at midnight?
THE SOC AND ITS REPORTING INFORMS GOVERNANCE OF IT SECURITY
Advanced users also link the systems to real time intelligence globally from leading bodies. Those commonly in use amongst leaders include the following:
Data feeds can be added to systems real time to maintain a full inventory of latest threats. Many sources exist and can be added in. Some of those in use in our sector include:

- AlienVault OTX – Malware, Malicious actor IP source. https://otx.alienvault.com/api

- SANS Internet Storm Centre – Top malicious IP from global honey pots. https://isc.sans.edu/tools/

- Malware Domains – Domains used by malware. CIS Center for Internet Security (cisecurity.org)

- National Cybersecurity Centre – CISP.
CYBER VULNERABILITY
TECHNOLOGY IS BEING EXPLOITED TO DECEIVE
Human behaviour and weaknesses are fair game
DEEPFAKE VOICE
The CEO of a large energy corporation transferred €220,000 to a Hungarian supplier. The CEO believed he was talking to his boss and acted swiftly to transfer the funds as directed. Only he wasn’t talking to his boss. Hackers successfully impersonated his boss’s voice, and the CEO believed it to be him. Most people think that they could tell the difference between someone’s real voice and an impersonation, but voice skins sound precisely like the individual being impersonated.
To mimic someone’s voice, recordings of that person’s voice must exist, and you’d be surprised at how often someone in your organisation is recorded. Webinars, YouTube videos, speeches, Ted talks, company training sessions, even smart speakers.
What is Deepfake and Why Is It a Major Cybersecurity Risk? Hitachi Systems Security – Your Cybersecurity Experts (hitachi-systems-security.com)
DEEPFAKE VIDEO
At the most basic level, deepfakes can be used to trick the facial recognition software that many consumers and businesses rely on for access control. This makes deepfakes among the top threats to cloud security.
Gearing Up Security for the Deepfake Era – Blog | GlobalSign
“Cyber investment is not just about threat
avoidance, having trained people and having formal qualifications has opened up new rental markets for us that are typically more regulated, like Defence and Government sectors.”
Response to cyber attack
PREPARATIONS IN THE EVENT OF AN ATTACK
Leader example – Crisis Management Planning
- Establish a framework
- Launch the crisis management process
- Emergency Approval Process
- Establish clear guidelines for escalation
- Appoint communications lead
- Develop a communications portion of existing incident response plan
- Map the stakeholders (customers, media, partners, regulators, employees, vendors)
- Develop draft media statements
- Host a table-top exercise
- Designate a Cyber Lead from Legal
- Review policies and public statements
- Conduct Cybersecurity Assessments and Tests (include direction from Legal Department)
- Conduct regular board briefings
- Manage third party vendors
> INFRASTRUCTURE
TRIAGE AND COMMUNICATIONS
“The First 48 Hours”
“If the worst happens, despite all the best prevention measures, leaders stress two things in the first period after an attack...”
- First … “Don’t react too much or too Make a calculated assessment and define an appropriate response”.
Attacks can come in many forms but one of the most serious types can be a “Ransomware attack”. In a systems denial situation, an immediate emergency response is needed but a process needs to have been put in place to assess and “Triage” the situation:
- Does this incident merit classification as an emergency?
- Is it ongoing? Should emergency response plans be activated now?
- Who can authorise disconnection from the network, the internet and closedown of a system that writes business?
- When will that permission to act be empowered?
- When will that escalation to higher levels of intervention (that may impact ability to do business) be triggered and who are the authorised decision makers?
- Who should be informed first and when?
- Is the attack financially or politically motivated?
Snapshot of reported attacks in a single month of 2022! …
July 2022. Hackers targeted Iran’s Islamic Culture and Communication Organization (ICCO). The attack took down at least 6 websites, placed images of Iranian resistance leaders on 15 additional sites, wiped databases and computers, and allowed hackers to obtain access to sensitive ICCO data.
July 2022. A hacker claimed to acquire records on 1 billion Chinese from a Shanghai police database and posted the data for sale online.
July 2022. Belgium’s Foreign Ministry accused China of a cyber espionage campaign against Belgian targets, including Belgium’s Ministries of Interior and Defence. A Chinese Embassy in Belgium spokesperson denied the accusations.
July 2022. Hackers targeted social media accounts owned by the British Royal Army. The attack included the takeover of the British Army’s Twitter and YouTube accounts.
July 2022. Hackers temporarily took down websites belonging to the Albanian Prime Minister’s Office and the Parliament, and the e-Albania portal used to access public services.
July 2022. Hackers breached a Ukrainian media company to broadcast on multiple radio stations that Ukrainian President Volodymyr Zelenskyy was in critical condition. Zelenskyy refuted the claims and blamed Russia for the attack.
July 2022. China stated the United States stole 97 billion pieces of global internet data and 124 billion pieces of telephone data in June, specifically blaming the National Security Agency (NSA)’s Office of Tailored Access Operations (TAO).
“Often, even with advanced monitoring and what is happening or what has happened and whether it is continuing. You have to stop and ask yourself… “What is really happening now, how serious is it? Should I step in and start shutting things down immediately that will impact our business? You can do more harm than the threat itself by responding too quickly, or in a panic, to stop a breach or a data loss”
If the worst happens, despite all the best prevention measures, leaders stress two things in the first period after an attack…
- Second … Communicate, communicate, communicate
Leaders believe that it is crucial to have a “First 48 hours response plan” to manage communications to staff, customers, suppliers and stakeholders. The plan may form part of the company’s overall disaster response and business continuity plan and stand as a cybersecurity Incident Management Plan.

A step-by-step “First 48” template has been adapted from model examples, offered by leader companies and is included at the end of this guide for user reference and further adaptation to their own circumstances.
“An attack is just like a real war in many ways. In the “Fog of War” you don’t know if something is really wrong. Assessment and clarity of understanding is key at the start of the onslaught. The decision to escalate to the 2 or 3 people at most in your organisation, who have the power to say “Stop everything” is a pivotal moment.”
CYBERSECURITY
IN CONCLUSION
Prepare for a secure future
THE RACE FOR GOOD IT SECURITY WILL NEVER END, BUT TO STAY AHEAD, EQUIPMENT RENTAL COMPANIES MUST:
- Know their assets, strengths and vulnerabilities
- Carry out risk
- Plan and invest
- Prepare, in case the worst
- Refresh and continuously improve
“The “Internet of Things” (IoT*) will never cease to bring new challenges and threats …
Security is the biggest concern in adopting “Internet of Things” technology, with concerns that rapid development is happening without appropriate consideration of the profound security challenges involved and the regulatory changes that might be necessary.
Most of the technical security concerns are similar to those of conventional servers, workstations and smartphones.
These concerns include using weak authentication, forgetting to change default credentials, unencrypted messages sent between devices, SQL injections, Man-in-the-middle attacks, and poor handling of security updates. However, many IoT devices have severe operational limitations on the computational power available to them. These constraints often make them unable to directly use basic security measures such as implementing firewalls or using strong cryptosystems to encrypt their communications with other devices – and the low price and consumer focus of many devices makes a robust security patching system uncommon.
CYBER STRATEGY
THE NEXT 3 YEARS FOR “LEADERS”?
No revolution but massively more maturity and digital enablement
- 1. Advancing up the maturity
- No revolution – “Leaders” are modest about their situation and consider they are not high enough up on the maturity scale.
- Although ERA Cybersecurity WG members are modest about their levels of maturity many are clearly advanced in many cyber aspects – but their focus remains on reinforcement, discipline and hardening of existing strategies and processes.
- No member appeared motivated to move strategy to leading edge or sunrise technologies such as Cyber AI, but several pointed to more demanding testing and penetration systems (such as “bounty pay per result systems”) which will inform and confirm maturity levels and drive further hardening of defences, develop better KPIs.
For those members in markets geographically close to the Ukrainian conflict, there has been an increased push to develop cyber defences
- 2. Develop cyber defence capability to support outward facing Digital
- Above all, members point to the drive towards digital enablement across the business, which means more and extended “open” platforms.
- They do not think this will create new vulnerabilities, but stress that early stage digitalisation has been data warehousing and internal process focused. The future thrust is increasingly on “end to end” data and platform integration with customers, equipment and other suppliers, where alignment and common cyber lines of defence end to end will be the key challenge.


